Have you heard of Cyber Essentials? The new UK government initiative to prove your company’s security credentials and give you a competitive edge.
The National Crime Agency will issue warnings about any new malware attacks that people need to be aware of.
An example is a Banking Trojan known as Cridex or a related variation, Dridex. Banking Trojans are malicious pieces of software which activate when the user uses banking websites. Cridex/Dridex will look for evidence of Bacs and FPS (Faster Payments Scheme) processing software on the PC. If it finds it, the virus will then download additional malicious software to exploit the processing software it has found.
Cridex/Dridex includes remote access software which allows the attacker to alter bulk payments files to change the destination of the funds. Dridex also includes a keylogger, software that records every keystroke you make. By using this software, the attacker may be able to collect PIN and password data for use in signing submissions once they have been altered.
To get infected you will have to click on a malicious link in an email, the most common being subjects such as a fake Amazon invoice, HMRC phishing campaign or ‘you’ve got a friend, click here. It is also possible that fake websites may download the virus when visited.
To minimise risk it is recommended that access to computers used for managing Bacs payments is carefully controlled and that they are not used for surfing the web or accessing email. You should also run Anti-virus scans regularly and particularly before submitting payment files.
Other actions you should take to protect your business:
- Make sure your Bacs submission computer has up to date software.
- If you are still using Windows XP then you may be at greater risk as any software problems with it that could be exploited by a hacker no longer get fixed by Microsoft.
- Never open attachments to an email unless you are satisfied the email is genuine.
- Ensure that all your iBB Users are aware of these threats and that they should report any suspicious activity immediately.
- Delete the email immediately
- Only visit website you trust and type the address into your browser rather than following a link on an email or website.
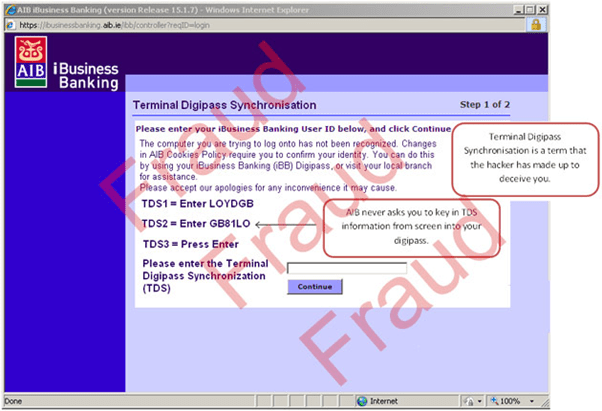
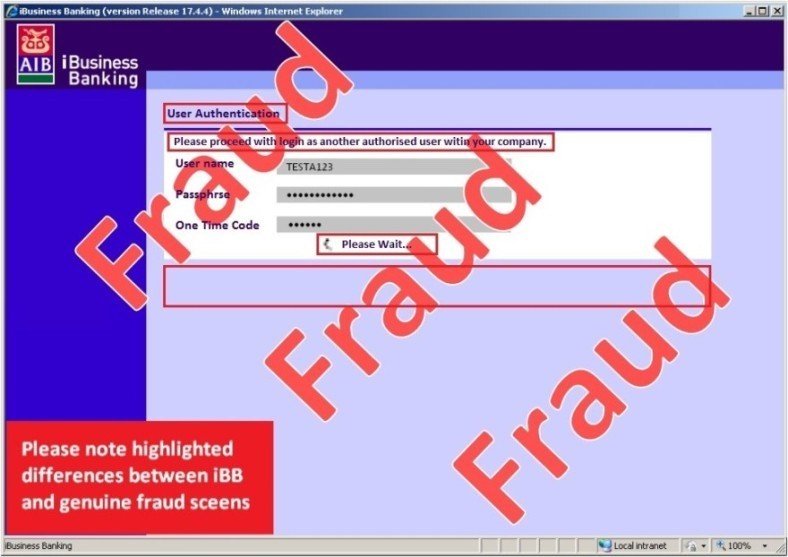
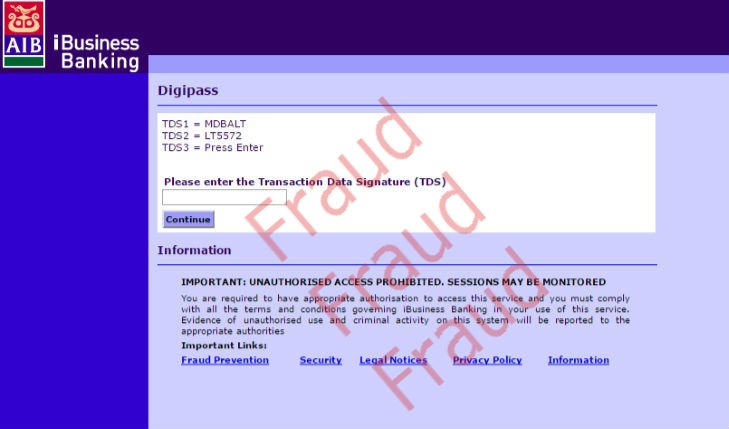
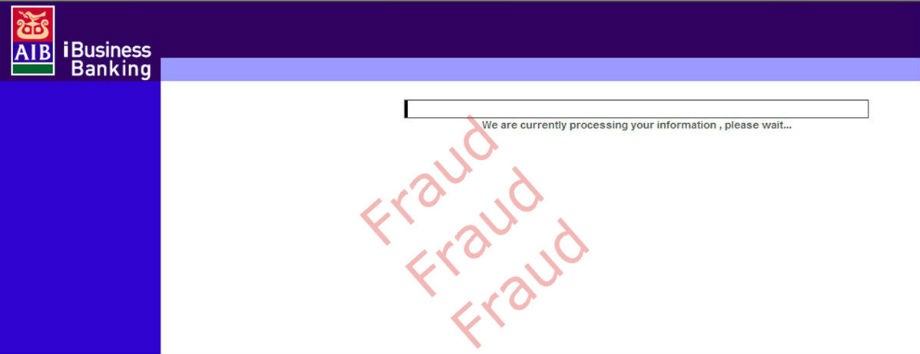
 While the screens below may look authentic, these are examples of a hacker attempting to get security information from you to make a fraudulent payment.
While the screens below may look authentic, these are examples of a hacker attempting to get security information from you to make a fraudulent payment. 